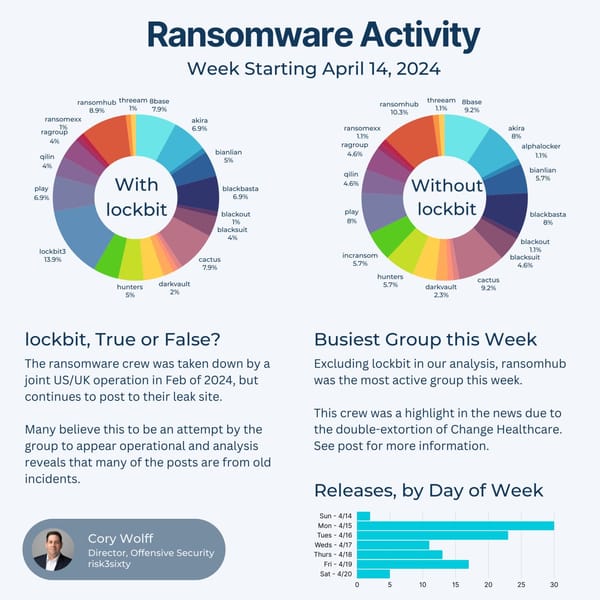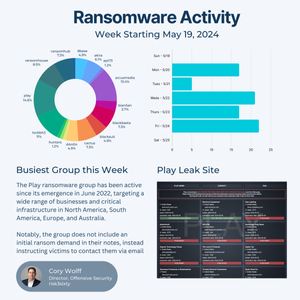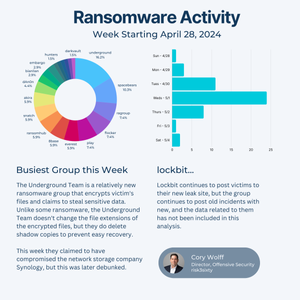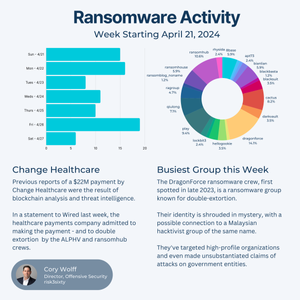
In February, Change Healthcare was targeted by the ALPHV/BlackCat ransomware group and despite an alleged $22M ransom payment, the data is now being held hostage for potential release.
But why? Double Extortion?
Ransomware groups have been known to extort victims twice - once to decrypt the files and then again with threats to release the obtained data.But the story is a bit more interesting than that.
ALPHV maintained a Ransomware-as-a-Service(RaaS) platform. Basically, a SaaS app for other ransomware crews to use. Other groups, known as affiliates, focus on gaining initial access and then use the RaaS platform to encrypt files, leave ransom notes, and handle payment.The ransom is then split. ALPHV was offering a 90% cut to affiliates using its RaaS platform.
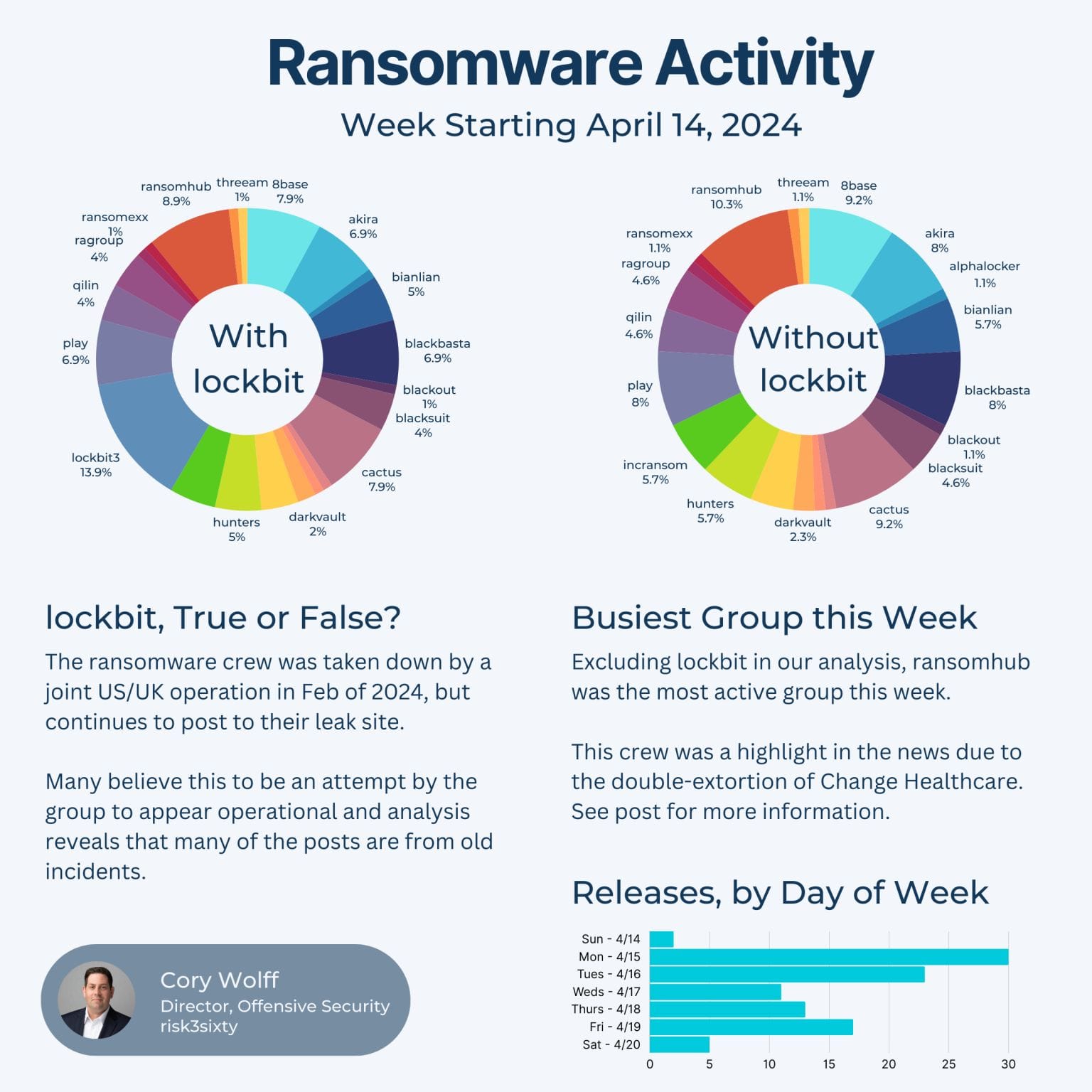
In this case, a group known as ransomhub (the busiest group last week minus lockbit) had achieved initial access to Change Healthcare and used the ALPHV RaaS platform.
Everything went as normal. Payment was made via the RaaS platform and then...
ALPHV skipped town. Exit scam. See ya later ransomhub and thanks for the $22M.
So now ransomhub is upset that they didn't get their cut and are demanding an additional payment to not release the data they exfiltrated.
This scenario underscores a harsh reality: paying ransoms does not guarantee safety from future extortion. The involvement of multiple ransomware groups illustrates a complex and evolving threat landscape where data can be weaponized repeatedly.
What do you think?