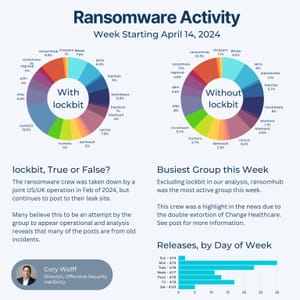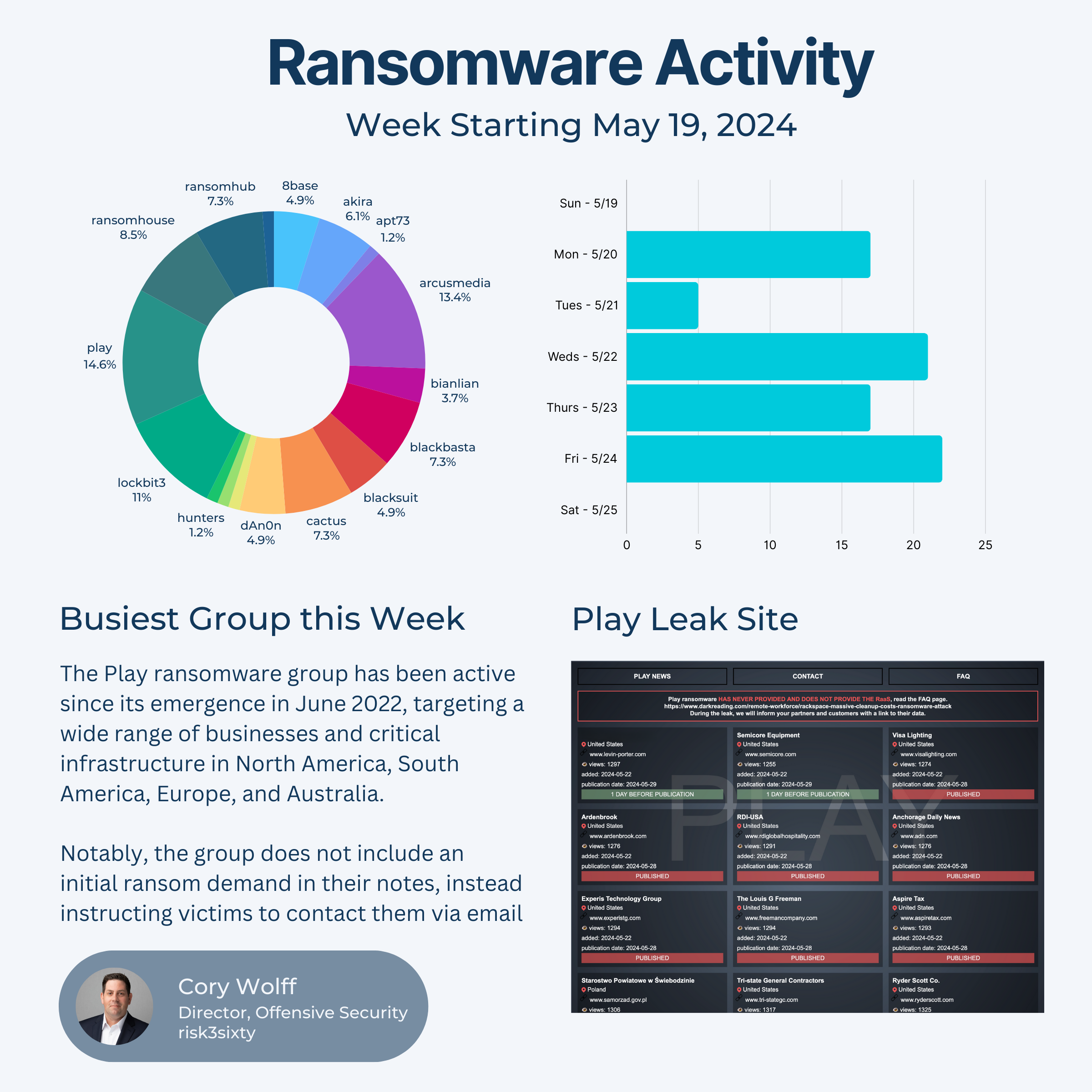
You might remember the Play ransomware crew from when they took down the city of Oakland...
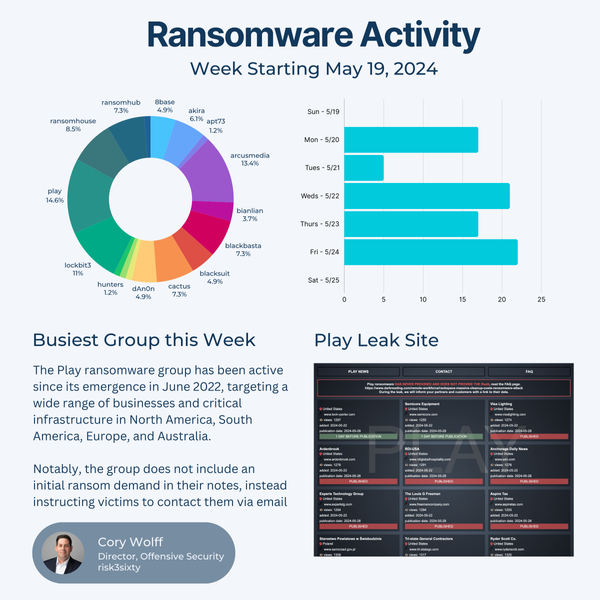
They have been very active since their emergence in June of 2022, targeting a wide range of businesses and critical infrastructure in North America, South America, Europe, and Australia.
In October of 2023, the FBI reported that the group had successfully breached approximately 300 organizations, including several critical infrastructure entities.
Like many other groups, the Play ransomware crew employs a double-extortion model, which involves exfiltrating data before encrypting systems. Victims are then pressured to pay the ransom under the threat of their data being published online. (See recent Change Healthcare attack).
Notably, the group does not include an initial ransom demand in their notes, instead instructing victims to contact them via email.
Recent high-profile attacks attributed to the Play ransomware group include incidents affecting the city of Oakland, the Judiciary of Córdoba in Argentina, and the German hotel chain H-Hotels.
If you were to take a look at the last 12 victims published on the Play leak site 11 of them would be US based...
Oh, and they're sure to dispel any rumors from news agencies that claim Play offers a Ransomware-as-a-Service. They're independent!