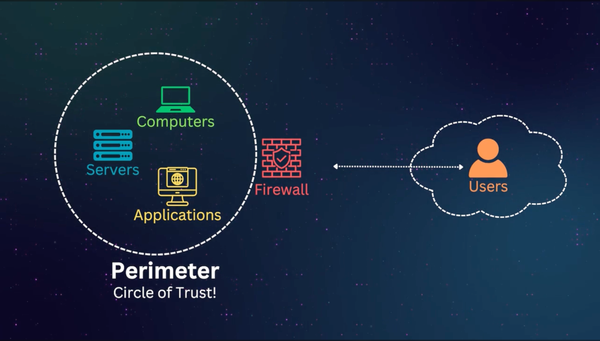
Zero Trust was created by John Kindervag in 2010 while he was a principal analyst at Forrester Research. It emphasizes 'never trust, always verify,' regardless of whether the request comes from inside or outside the network.Notably, incidents like Operation Aurora and Google's development of BeyondCorp highlighted the need for this approach. These events demonstrated the vulnerabilities of traditional perimeter-based security models and underscored the necessity of continuously verifying every access request.
🔍 Key Principles of Zero Trust:
Never Trust, Always Verify - Continuous and dynamic verification.Least Privilege - Only granting the minimal access needed.Assume Breach - Planning for the worst-case scenario and segmenting systems to minimize damage.
Why can't you simply buy Zero Trust? It’s not a one-size-fits-all product but a comprehensive approach that involves cultural changes, continuous improvement, and the integration of multiple security measures tailored to your specific environment.
Implementing Zero Trust involves a long-term strategy, ongoing assessment, and adaptation to evolving threats. Companies must commit to incorporating best practices and continuous learning to effectively secure their assets.